Powershell/Graph | Assign Graph Application Permissions
The Azure Active Directory module is not supported in newer Powershell versions (7+) and will be retired at any time after June 30, 2023. I used a script by maayanlux from the Azure Cloud AI Blog to assign Graph Application Permissions in the past, but couldn’t get it working with newer Powershell Versions.
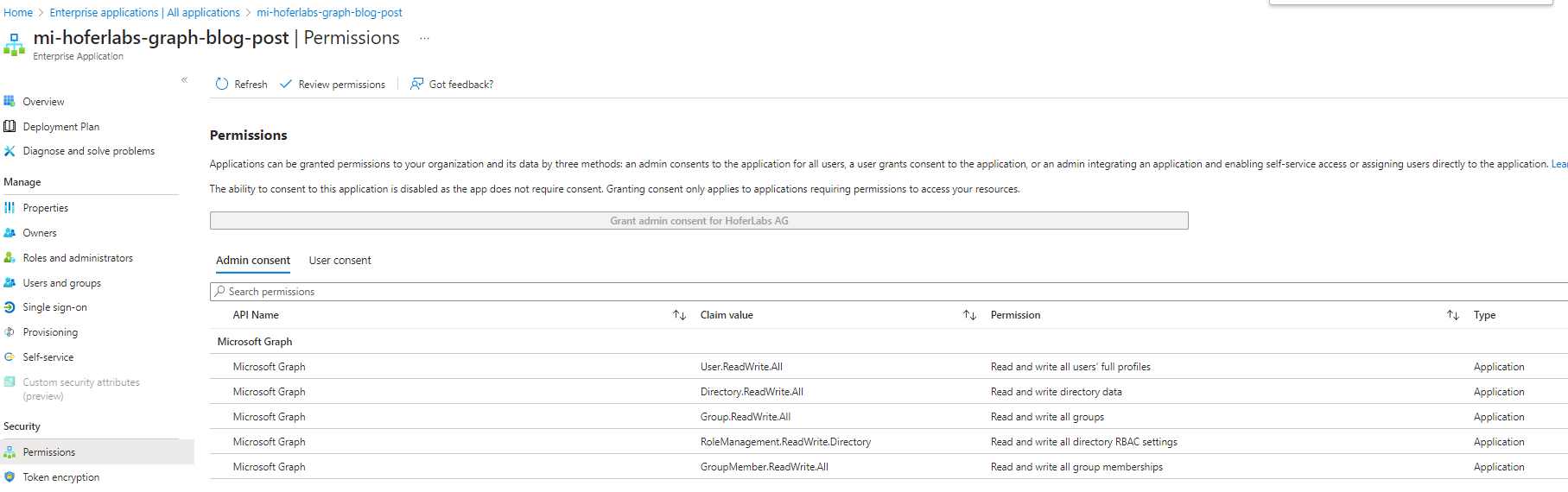
The new way is to use the Graph Module (/API). I found a script from Jannik Reinhard but it doesn’t support multiple permissions. Let’s combine them… I also added a verify step which shows current assigned permissions and when they were assigned…
assignGraphPermissions.ps1assignGraphPermissions.ps1"####################################################################################################################################" "# hoferlabs.ch #" "# assign Graph application permissions using Graph Powershell Module #" "# Version: 0.1 #" "# Inspired by https://jannikreinhard.com/2023/04/09/how-to-start-with-azure-automation-runbook-to-automate-tasks-in-intune/ and #" "# https://azurecloudai.blog/2023/03/22/azure-ad-powershell-to-microsoft-graph-powershell/ #" "####################################################################################################################################" # edit here # for enterprise applications / managed identities: use the object id of the enterprise application $strAppId = "c2280552-0c9a-43e7-8f44-e862d30c8058" $arrPermissions = "User.ReadWrite.All", "Group.ReadWrite.All", "Directory.ReadWrite.All", "GroupMember.ReadWrite.All", "RoleManagement.ReadWrite.Directory" # do not edit $strGraphAppId = "00000003-0000-0000-c000-000000000000" Connect-MgGraph -Scopes Application.Read.All, AppRoleAssignment.ReadWrite.All, RoleManagement.ReadWrite.Directory "get graph app..." $objGraphApp = Get-MgServicePrincipal -Filter "AppId eq '$strGraphAppId'" "assign permissions..." ForEach ($strPermission in $arrPermissions) { " assign permission $strPermission..." $objRole = $objGraphApp.AppRoles | Where-Object { $_.Value -eq $strPermission } $objResult = New-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $strAppId -PrincipalId $strAppId -ResourceId $objGraphApp.Id -AppRoleId $objRole.Id } "verify permissions..." $arrRoleAssignment = Get-MgServicePrincipalAppRoleAssignment -ServicePrincipalId $strAppId ForEach ($objRoleAssignment in $arrRoleAssignment) { $objRole = $objGraphApp.AppRoles | Where-Object { $_.Id -eq $objRoleAssignment.AppRoleId} " assignment for app role $($objRole.Value) was created on $($objRoleAssignment.CreatedDateTime) (ID: $($objRoleAssignment.AppRoleId))" }
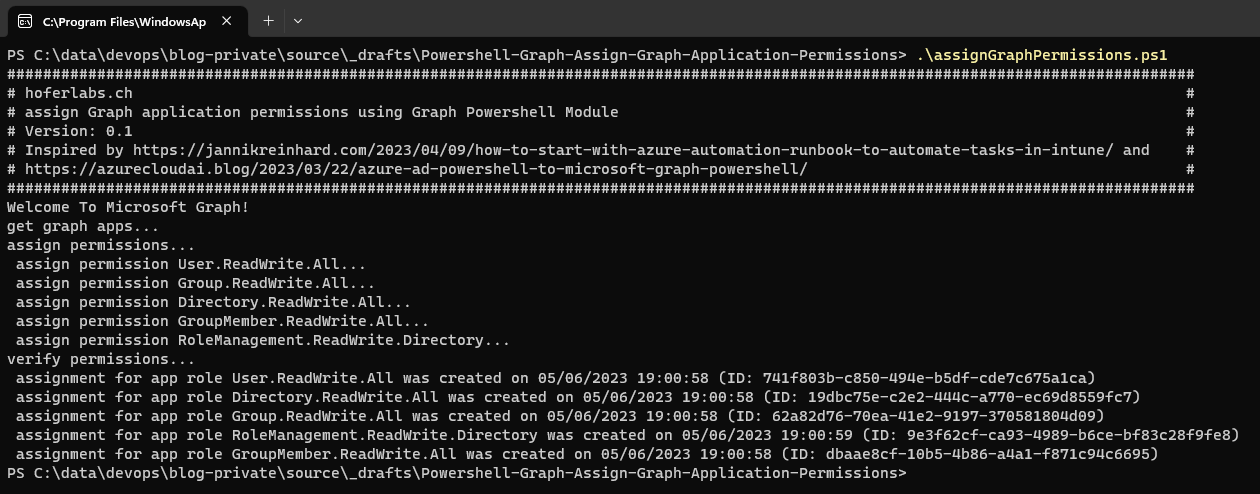
Script outputs for assigning permissions to a managed identity:
Permissions: